Whenever we need to improve our online privacy, we often have two options: VPNs or Tor. Most internet users will adopt the former, while more tech-savvy individuals will employ a mix of the two.
But in some cases, MixNet, another anonymity solution that's not widely adopted yet offers powerful privacy features, can be better. So what is it? How does it work? And how does it compare to Tor and VPNs?
What Is MixNet?
MixNet is short for Mix Network, a technology that helps keep information sent over the internet private and secure. It does so by mixing up data from different sources before sending it to its destination. This makes it hard for an outsider to find the data's source and destination.
While most internet data is encrypted and its content protected by protocols such as TLS and SSL, it contains metadata that outsiders can analyze and use to identify the senders and receivers. A MixNet implements metadata shuffling to protect users' privacy.
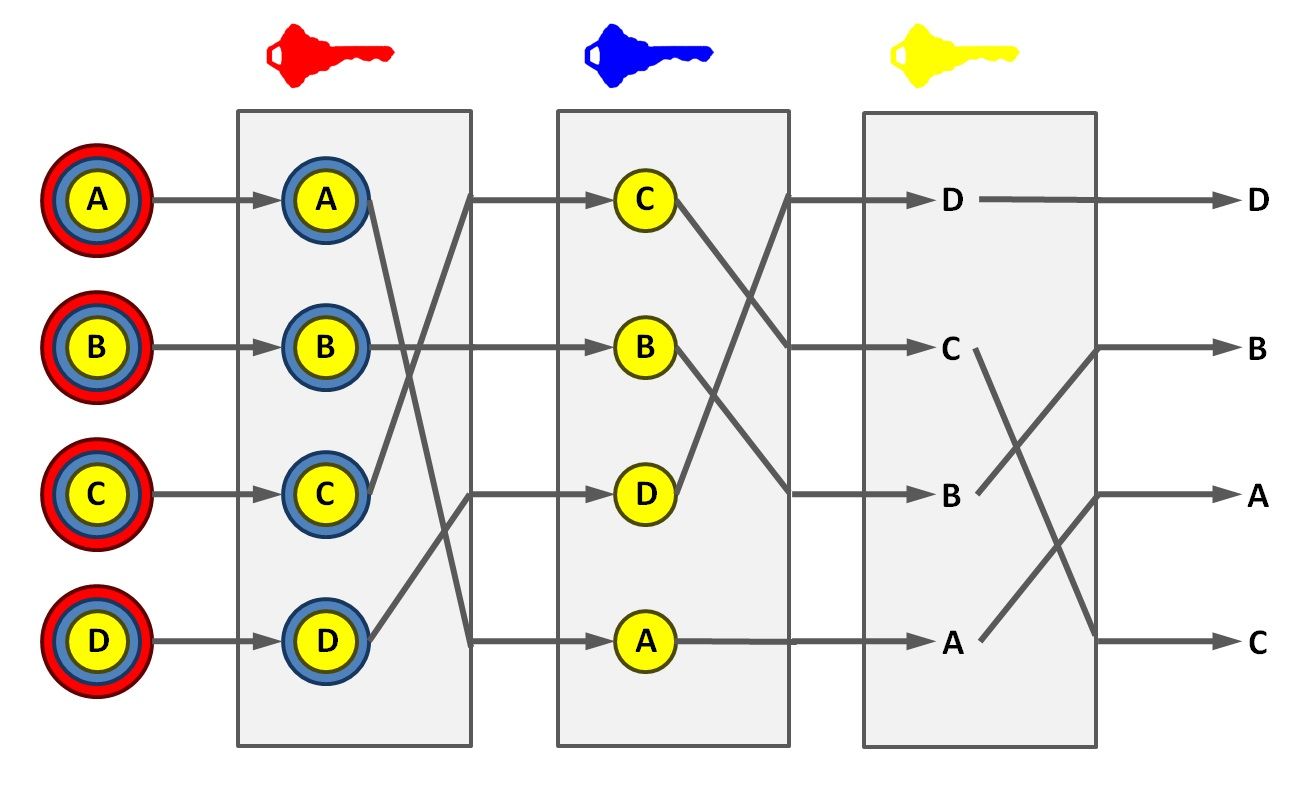
How Does a MixNet Work?
A MixNet applies protocols that mix and shuffle data from different sources while sending it through a network of interconnected nodes. It mixes metadata such as geographical location, sender and receiver IPs, message size, and send and receive times. That makes it difficult for an outsider to get any meaningful insights that could help reveal the users' identities or predict the contents of the data.
MixNets are made up of two components:
- PKI (Public Key Infrastructure): The system that distributes public key material and network connection information required to operate the MixNet.
- Mixes: Cryptographic routes that are part of the mix network. They receive incoming messages, apply cryptographic transformation, and mix data to prevent observers from linking incoming and outgoing messages.
The PKI system powers the mix network, and if compromised, the entire network will be at risk because the attacker can replace nodes with ones under their control, allowing them to take over. That's why it needs to be decentralized.
Mixes break down data into bits and transform it into cyphertext, resulting in bitwise unlinkability. The cyphertext is then relayed through a mix cascade (fixed order of nodes) before reaching the destination. In addition, mixes add latency to prevent attacks based on timing patterns.
While one mix node is sufficient to address privacy concerns, it risks being a single point of failure. So, at least three mixes are used, with each independent node providing an added layer of anonymity and contributing to the collective resilience of the network.
MixNet vs. Tor
Tor is another technology designed to enhance online privacy that's more widely adopted. However, it uses a different approach to achieve anonymity.
While a MixNet works by mixing data to make it hard to link the origin and destination, Tor employs a technique known as onion routing, where data is encrypted in layers and routed through a series of relays operated by volunteers before reaching its destination.
The relays in a Tor network only function to encrypt the data with unique keys without knowing where the traffic comes from and where it's headed. Each layer of encryption makes it difficult to trace the origin and the destination.
However, by design, Tor requires exit nodes—the final relays in the network—that decrypt the last layer of encryption and send it to the destination. This factor introduces a security concern if the final relays are malicious.
The unique approaches to online anonymity used by MixNets and Tor result in different strengths and weaknesses. For instance, MixNets are good at preventing timing correlation and confirmation attacks, while Tor is effective against website fingerprinting and Sybil attacks.
In addition, Tor is more resilient due to a larger network and user base, while MixNets have lower latency due to fewer network relays involved. The choice between the two depends on specific requirements, such as the desired level of anonymity, latency tolerance, and network size.
MixNet vs. VPN
VPNs (Virtual Private Networks) are perhaps the most widely adopted online anonymity and security platforms, partly due to their ease of setup and a large pool of service providers on the market.
VPNs create an encrypted tunnel between the user and a server. The tunnel encrypts the user's internet traffic, hiding their personal data, location, and browsing activity, and so prevents an outsider from eavesdropping.
This approach is unlike MixNets which cryptographically transform bit-sized pieces of data before mixing them and passing them through multiple relays to make it hard to link the data with the involved parties.
VPNs are effective in cases where one wishes to hide their location, securely connect to public Wi-Fi, access region-restricted content, and maintain general privacy while browsing the internet. However, since they have to rely on a centralized VPN server infrastructure, they are subject to trust issues and privacy concerns.
On the other hand, MixNets are more effective in cases where strong anonymity and metadata protection are needed. They also have less latency and a more decentralized architecture than VPNs, which depend on centralized servers.
Limitations of MixNets
MixNets also face several limitations that can impact their effectiveness and practicality...
- Latency: The mixing process delays messages before they are forwarded. While this is essential to prevent timing correlation attacks, it can impact the user experience for real-time applications that require low-latency interactions.
- Network scalability issues: As the number of users and messages increases, maintaining the required mix nodes and managing the process becomes more complex. Network scalability can be a challenge, especially in large-scale applications of MixNets.
- Bandwidth overhead: The mixing process increases the size of data packets, leading to higher bandwidth consumption than direct communication. This can be a concern for users with limited bandwidth or applications requiring efficient data transfer.
- User inconvenience: MixNets may require users to install specialized software or use specific protocols, which could hinder widespread adoption. User-friendly interfaces and seamless integration are necessary to encourage user participation.
- Sybil attacks: MixNets can be vulnerable to Sybil attacks, where an attacker creates many fake nodes to gain influence over the network. This could lead to message redirection, manipulation, or privacy breaches.
Although MixNets offer strong privacy protection, their limitations make them less convenient options for online privacy. However, several upcoming technologies are addressing these limitations. For instance, HOPR uses P2P networking of nodes, which increases scalability, while Nym arranges mix nodes into layers, forming an architecture that offers more scalability without compromising anonymity.
Should You Use MixNets?
Whether to use MixNets to improve your online privacy or not depends on your specific needs, your willingness to tolerate latency and bandwidth overhead, and the compatibility of your applications.
Mixnets are suitable if you're particularly concerned with staying anonymous, and if you have applications that are not time-sensitive; but they're unsuitable if you prefer user-friendly solutions or use real-time communication applications. Either way, it's important to carefully evaluate the advantages, limitations, and considerations before deciding whether MixNets are necessary.