Our gadgets aren't just tools that make our lives easier. They hold so much personal data and vital information that keeping them secure is essential. Fortunately, Apple devices are excellent in this department.
Well, Apple doesn't just make devices sleek and stylish devices. The company puts a lot of effort into ensuring your privacy, security, and convenience. And here are all the features that make that possible.
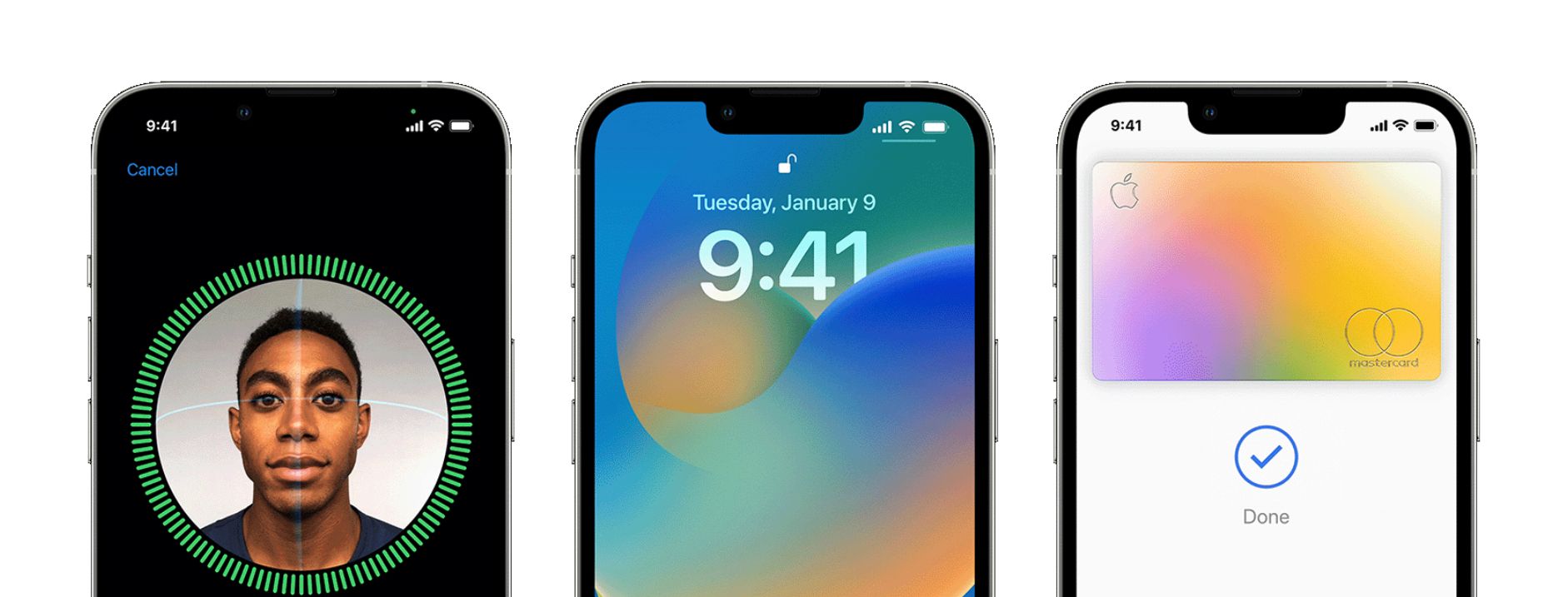
1. Face ID and Touch ID
There's no guarantee that our devices won't end up in another person's hands, like a nosy colleague or a curious family member. And there's a very slight chance that with a mere passcode or password, they might guess their way into unlocking your phone or laptop.
But it's harder to duplicate your biometric features. You can't guess your way into that. With Face ID and Touch ID, there's an extra layer of security for your Apple devices, ensuring no one else but you can gain access. Plus, it's convenient and efficient.
And it's not just access to your primary device you can protect. You can use workarounds like Shortcuts to lock any app on your iPhone.
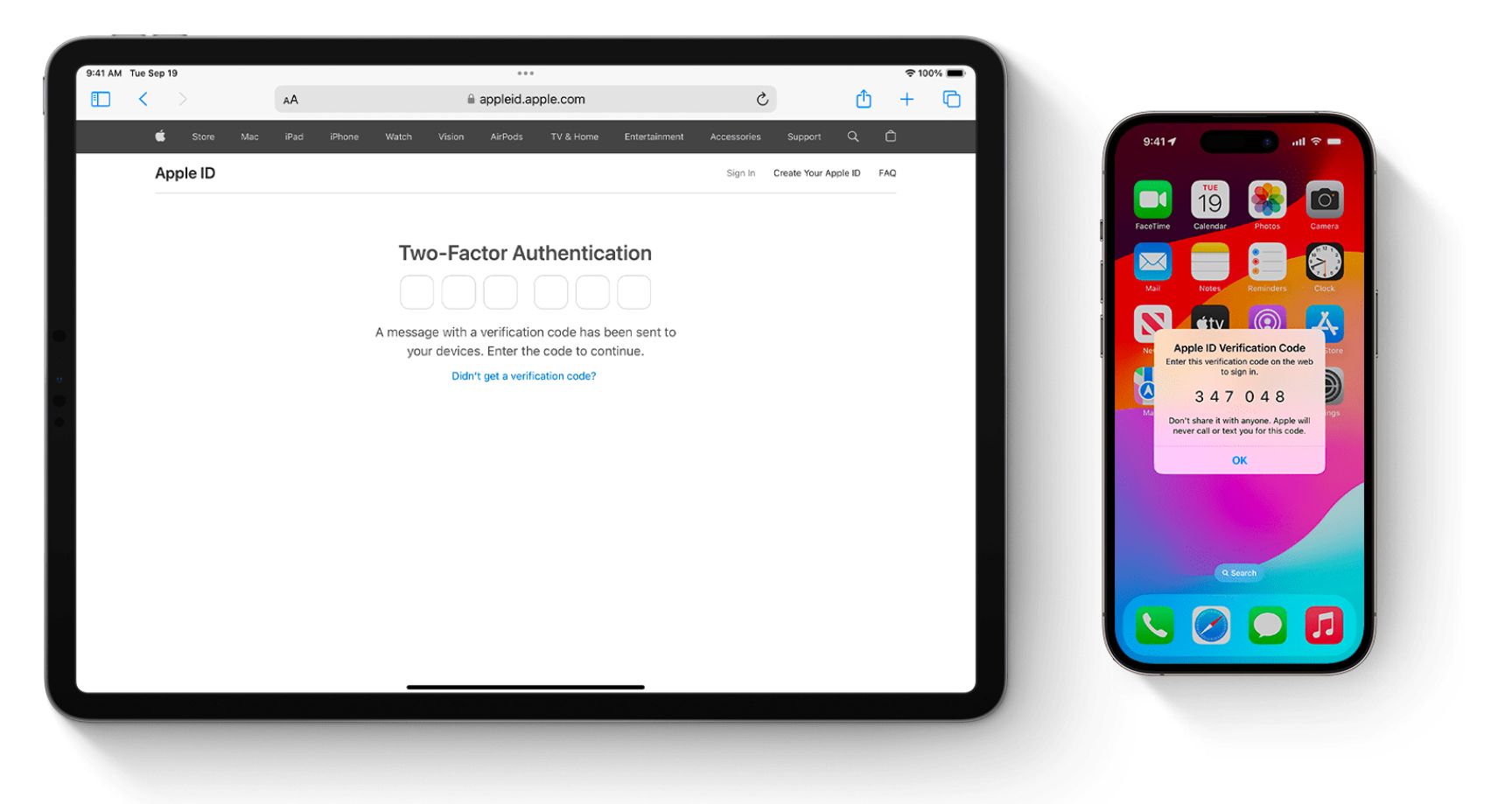
2. iCloud Two-Factor Authentication
Again, it's scary to think of your data in the wrong hands. You don't want any of your sensitive information getting swiped. To protect you and ensure your privacy, Apple has added another layer of defense that requires you to provide extra verification whenever you log in to your Apple ID account.
This means that whenever there is an attempt to log in to your Apple ID on a new device or the web, Apple will notify you. You will have the option to approve the login or block any suspicious attempt.
A verification code would be sent to a trusted device like your iPhone. However, if you haven't set up a trusted device, you'll receive a code on your registered phone number. However, you should set up two-factor authentication for your Apple ID to prevent security risks.
3. App Store Vetting Process
Apps define our experiences across all devices. You need them to browse the internet, attend virtual meetings, and correspond or collaborate with your colleagues—the list goes on. Cyber-criminals understand this and often design apps as Trojan horses with which they introduce malware into your devices.
Apple takes extra precautions before including apps in its store. Whenever a developer submits their app, there's a strict vetting process to ensure that it doesn't contain any malicious elements that can compromise your safety and security.
But Apple can only guarantee the safety of your data and devices through channels it controls. If you choose to download apps from other sources, please know that sideloading unofficial apps is risky.
5. Safari's Intelligent Tracking Prevention
You generate so much data every day that several companies find valuable. This has accelerated the culture of data mining, which can sometimes be illegal. Even though companies provide you with essential software and services, they shouldn't be snooping around and collecting sensitive information without your consent.
Safari helps you maintain your online privacy while browsing. It doesn't share your data with Apple and is transparent about how it manages your data. When you visit other websites, it stops them from getting all up in your business, monitoring your activity, and collecting your data. And that's just one of the many ways Safari helps boost your privacy and security.
6. End-to-End Encryption in iMessage and FaceTime
Have you ever wondered what end-to-end encryption is? It's an essential security feature that protects your correspondence from prying eyes. This is a key part of the built-in iMessage and FaceTime apps on your Apple devices.
End-to-end encryption ensures that you can send and receive messages without worrying that a third party on the internet could take a peek. All your conversations are protected, even from Apple.
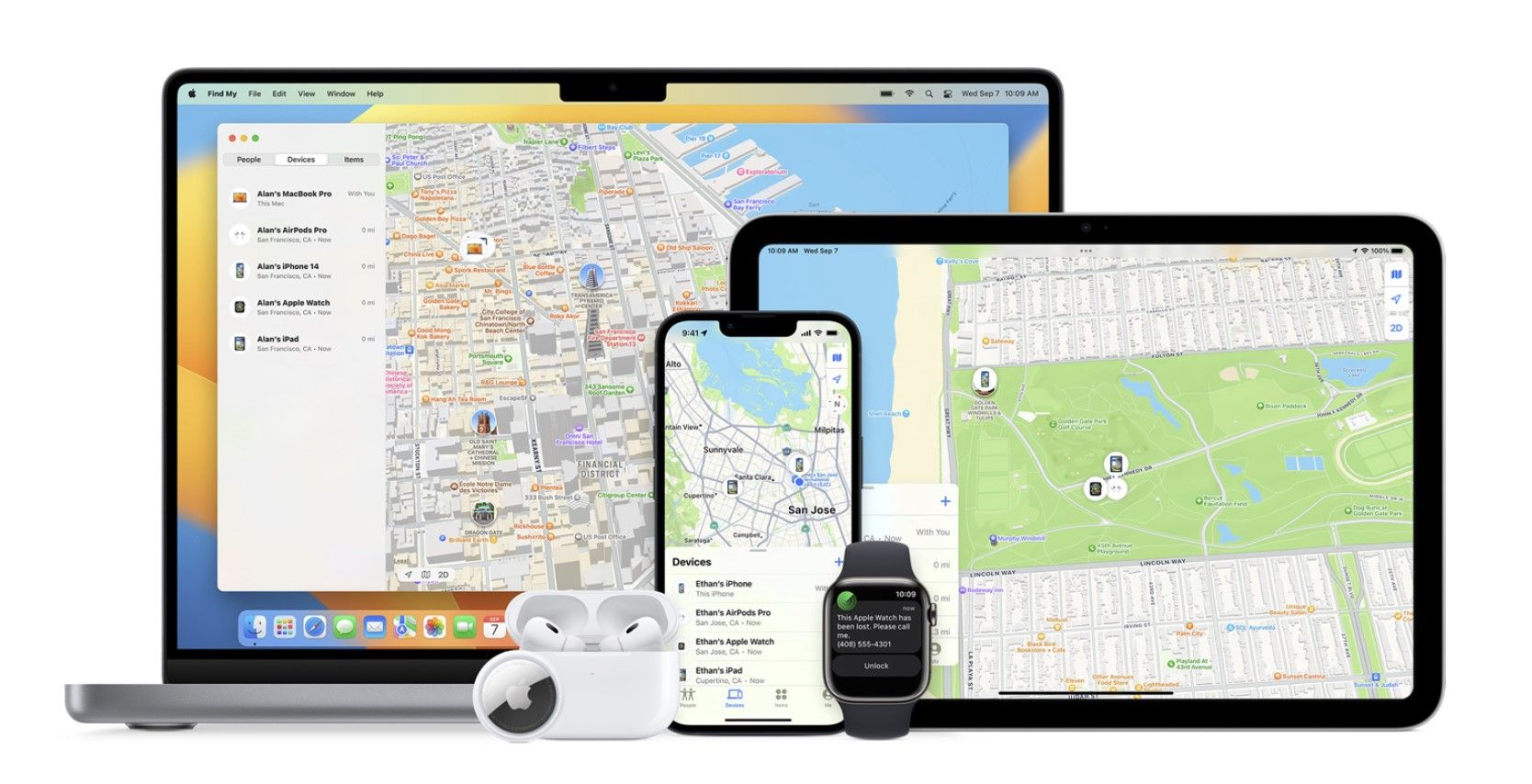
7. Find My Device and Activation Lock
There are very few things as scary as losing your device. Apple is in the business of ensuring your convenience, so with the Find My app that's available across all devices, it's a lot easier to track and locate any missing Apple device, provided it's logged in to your Apple ID. You can spot its location on the map, whether the device is online or offline.
Another vital security feature that accompanies the Find My app is the Activation Lock. Let's assume that your Mac has been stolen; Activation Lock makes it difficult for the thief to sell your device for some quick cash. Your device can be locked remotely, and you can only deactivate the lock with your login information or a bypass code.
This prevents another person from gaining control of your device even if they have physical possession of it, and it stops them from swiping vital information. This feature is available on iPhones, iPads, Apple Watches, and modern Macs, so it's worth checking if your Mac is protected by Activation Lock.
8. Secure Enclave for Data Protection
Another component of Apple devices, hardware this time, that keeps your sensitive data under lock and key is the Secure Enclave.
The Secure Enclave generates a unique encryption key when you set up a new Apple device, like an iPhone or Mac. This key is then used to encrypt sensitive data such as your fingerprint or facial recognition data for Face ID. This key never leaves the Secure Enclave; it remains isolated from the rest of the device's components.
So, even if a hacker gains access to your device's storage or memory, they won't be able to retrieve this key. That makes it extremely difficult for an unauthorized party to decode your sensitive information, whether that's biometric data, passwords, or encryption keys. This level of security is one of the reasons most Mac users never switch to Windows.
9. App Permissions and Transparency
When you install an app from the App Store, it has to ask for your permission before it can access your device's camera, microphone, or location. You can choose to grant or deny access from a simple pop-up. As for apps that ask for your location data, you can restrict access in such a way that they don't continuously track your location in the background.
Additionally, Apple's App Tracking Transparency feature ensures apps can't track your activity across other apps and websites unless you allow them. When an app wants to track you, it has to present a prompt asking for your permission.
Also, by turning on App Privacy Report on your iPhone or iPad, you can get an insight into which apps have accessed your data and when and check whether any app is sharing your data with a third party.
10. Sign In With Apple
It takes you less time to use Sign in with Apple to sign up for a website, app, or service. And you don't have to bother filling out forms, verifying your email address, and creating different passwords for every online account you create.
Additionally, you can use the Hide My Email feature to mask your personal email address and safeguard your privacy.
Apple Is All About Convenience and Security
As technology evolves, the level of security risks and threats increase. Cybercriminals are getting better at targeting our gadgets in hopes of swiping valuable data. Big tech companies are also curious to see what you do online, so they know what to sell to you and how to better advertise to you.
In this ever-evolving digital landscape, Apple stands out by creating an ecosystem that puts your privacy and security at the forefront. Apple devices may be popular for being sleek and stylish. But under the hood, they're equipped with robust security measures that keep your data secure and allow you to use them with peace of mind.